Security in IoT – Distributed Danial of Service (DDoS) II
This post is the second part of the last post and will describe the architecture along with characteristics of Malware especially Mirai and Hajime.
Characteristics of IoT malware
As mentioned before, the IoT device should get the Malware in order to participate in DDoS attacks. Most of the malwares are Linux based and has limited or no side effects on the performance of the host. They become active and perform DDoS on certain command from its botnet herders. However, the volume of traffic floods generated by IoT botnets are very high, in the orders of 100 Gbps or higher, in comparison to conventional PC botnets and apart from generating commonly used traffic floods, namely, HTTP, TCP, UDP traffic, some IoT botnets generate unconventional traffic like GRE traffic and use uncommon ”DNS water torture” technique during DDoS attacks. It should be considered that most IoT malware does not use reflection or amplification techniques to launch an attack, so it is much difficult to recognize and mitigate the attack using conventional methods. Besides, they usually support different architecture such as ARM, MIPS, x86/x64, MIPSEL, etc which enable malware to cover a wide range of microcontrollers. LightAidra, Darlloz, Mirai and Hajime malware fall into this category and in the rest of this section important features of Mirai and Hajime will be introduced and compared.
Mirai Malware
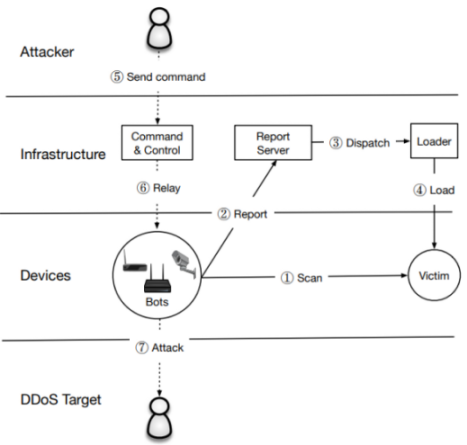
Mirai is a software that turns networked Linux devices to the controllable bot. So remote computer or malicious server can access them. In October 2016 hackers accessed thousands of IoT devices and took control of them and used them to flood the servers of important internet companies with malicious traffic. Today, Mirai Botnet is not limited to the IoT devices, which are not secure enough, but also they can be dangerous for unpatched Linux Server through the vulnerability in Hadoop Yarn[1]. The Apache Hadoop software library is a framework that allows for the distributed processing of large data sets across clusters of computers using simple programming models and Apache Hadoop YARN is the resource management and job scheduling technology in the open-source Hadoop distributed processing framework[2]. Due to the Hadoop YARN vulnerability, the attacker can run any command from Shell and therefore Linux malware can be installed[1]. One of its features is that Mirai botmasters that target Linux servers no longer need to tailor their malware for strange architectures, they assume their targets are using x86 and rather than rely on the bots to propagate, the attackers have shifted their tactics to issuing exploits themselves. A relatively small number of attackers are using custom tools to exploit the Hadoop YARN vulnerability and deliver Linux malware. Moreover, even if the victim Hadoop YARN server is not running the telnet service, the Mirai bot will attempt to brute-force factory default credentials via telnet. Also, it should be considered that Linux servers in data centers have access to more bandwidth than IoT devices on residential networks, making them much more efficient DDoS bots. A handful of well-resourced Linux servers can generate attacks that compete with a much larger IoT botnet[3] and [4]. As illustrated in Fig. 1, in (1) infected IoT devices (Bots) start scanning the IPv4 address space for devices that run telnet or SSH and try to log in (brute-force) using list of 62 credentials which are hardcoded in Mirai code, once successful, the bot sends (2) the IP of the victim along with credentials to the Report Server which asynchronously triggers (3) a loader to infect the device (4). The new bot starts scanning for additional victims and accepts the command from C & C (Command and Control) server (6).
Hajime Malware
Hajime Malware is like Mirai and uses unsecured open Telnet ports along with a dictionary of default passwords in order to log in. It uses the exact same username and password combination that Mirai uses, plus two more[6]. As shown in Fig. 2, a node on Hajime network starts scanning the random IPv4 addresses on the public internet and discovers a device which accepts connections on TCP port 23 which is designated port for telnet[7] and TCP/5358 (WSDAPI). This figure represents the overview mechanism of Hajime for infecting MikroTik Routers[8].
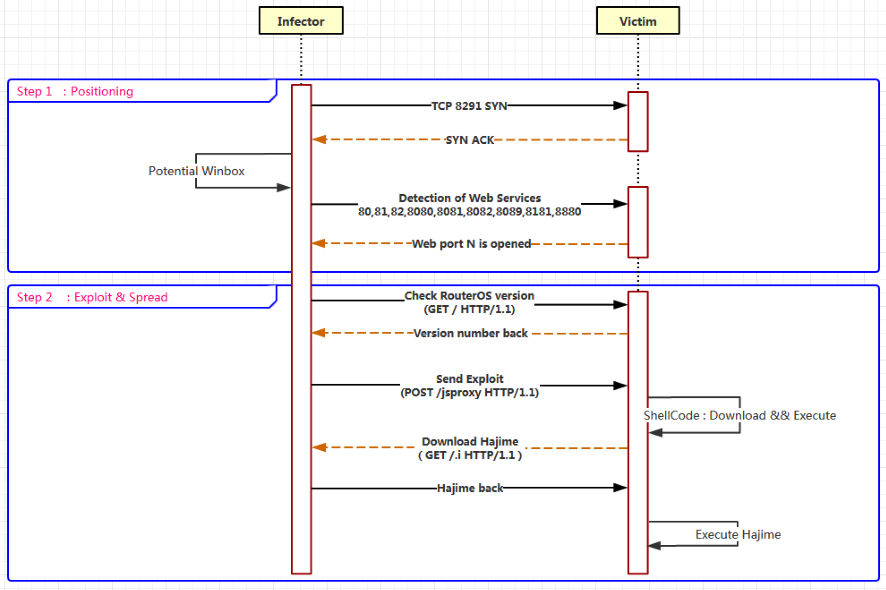
It seems that Hajime does improve the security of the IoT device against attacks such as Mirai, in fact it will prevent further access to the device through filtering ports known to be abused by IoT bots such as Mirai[9] and are TCP/23 (telnet), TCP/7547 (TR-069), TCP/5555 (TR-069), TCP/5358 (WSDAPI). It does not contain any module or tool for DDoS attacks, instead, it has only methods for extending itself and BitTorrents DHT protocol for peer discovery and uTorrent Transport Protocol (uTP) for data exchange. Table 1 summarizes some of the features of Mirai and Hajime.
| Properties | Mirai | Hajime |
|---|---|---|
| Attack Pattern | Telnet 23/2323 | Telnet 23,TCP/5358 |
| Telnet Credentials | Hardcoded | Same as mirai+2 |
| Scan & Propagation | like Qbot | like Qbot[7] |
| Access Server | IP in hardcoded in source code | P2P Connection using bittorrent |
| Usages | DDoS | No attack, but can provide DDoS-as-a-service or deployment services |
| Date of release | Oct. 2016 | work on it starts before 2013[7] |
| Open Source | Yes | – |
| Supported Architecture | ARM, MIPS, x86, PowerPC, etc | Linux based platforms |
Table 1. Comparison of Mirai and Hajime
But, what would be the purpose of Hajime? In [7], researchers have 4 consideration about the purpose of Hajime:
- Providing DDoS as a Service platform
- A distribution platform for other payloads or deployment service for future botnets
- Extraction of confidential data, such as financial data, from local networks
- It could be considered just as a research or hobby project.
Continue Reading: Security solution for IoT communication protocol
Last post: Distributed Danial of Service (DDoS) I