Security in IoT – Distributed Danial of Service (DDoS) I
The goal in this post and the next one is to describe Distributed Danial of Service attack, its architecture, and the most common Malware for DDoS in IoT devices.
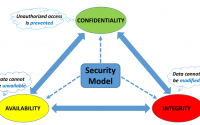
What is Danial of Service
One of the most popular attacks is the Denial of Service attack in which the attacker tries to make the server or network unavailable to legitimate users. This can be done by disrupting services on the server side, for example, the attacker will flood the server or service/resource by so many requests and consequently, the system will be overloaded, and prevent services to be fulfilled. There is plenty of DDoS software such as Slowloris, LOIC (Low Orbit Ion Canon), GoldenEye and etc. Although IoT devices don’t have computation power as PCs and servers have, they can participate in such attacks to provide network traffics.
Difference between DoS and DDoS attack
In DoS attack which is shown in Fig. 1, just one user/computer do the attack against the server and, basically, it is not dangerous anymore, because the server will detect it and will close the connection with that specific user/computer.
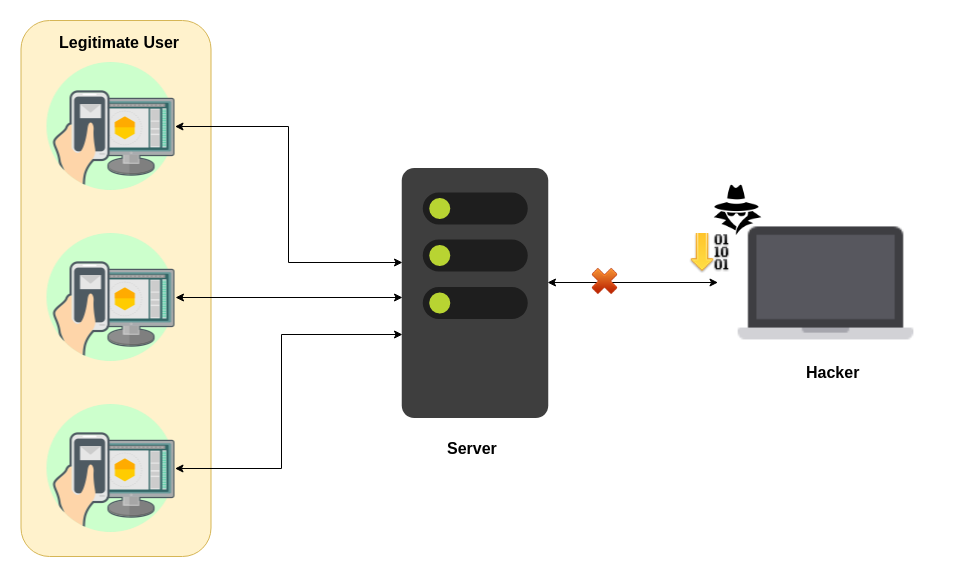
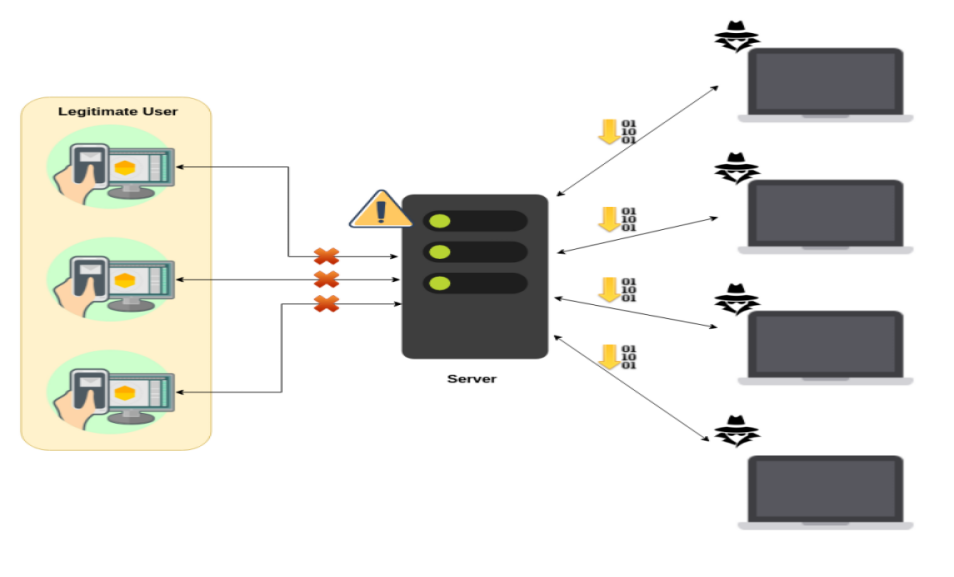
What if a DoS attack comes from multiple sources simultaneously? This attack called DDoS or Distributed Denial of Service which shown in Fig. 2 and Fig. 3. In this attack, multiple computers try to overload the server by requesting services. The result is that legitimate users can not access services.
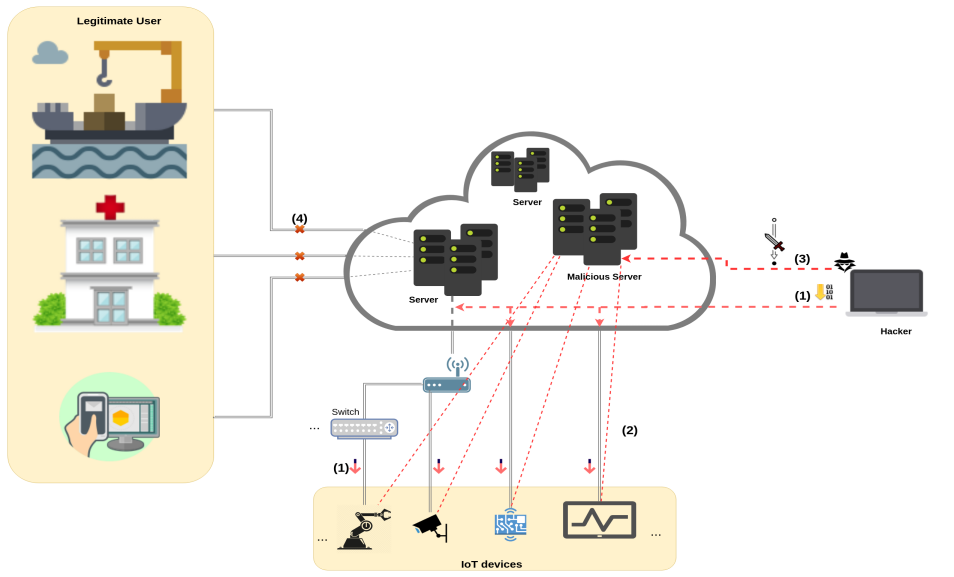
But how to orchestrate IoT devices in order to participate in the attack? The simple answer would be using malware(Malicious Software). So if the IoT device gets malware (become a bot) and joins the network of infected devices which called Botnet. Then they will get data and time of attacking to the specific server from a malicious server. Fig. 5 illustrates an example of a DDoS attack through in which an attacker tries to upload malicious firmware to IoT devices either by hardware or software hacking. By doing this step the IoT device may not be accessible or do not complete its job, and instead starts communicating with the malicious server or download malware and become botnet. At this stage, the attacker can control the IoT device and it can get time and date for participating in DDoS attack. In the last step, attacker or malicious server ”attack command” and IoT devices start overloading a server by requesting services and the result is that legitimate users will lose connection to the server or services.
Famous DDoS Attack
In the last few years, hackers target websites and services some of the giant companies with DDoS attack, for instance on Feb. 28, 2018, GitHub was hit with a sudden onslaught of traffic that clocked in at 1.35 terabits per second[1]. Or on December 31 of 2015, the BBC website was successfully taken down by a group known as the New World Hacking. Their massive DDoS attack took down the BBC site and even affected Donald Trump’s homepage as well[2]. Also, a lot of popular online services including Netflix and Twitter use DynDNS as a backbone to grant users access to their platforms. Due to this unprecedented DDoS attack executed by the Mirai botnet, none of these services were operational for nearly 24 hours[2]. And the PopVote DDoS attack was carried out on June of 2014 and targeted the Hong Kong-based grassroots movement known as Occupy Central. DDoS attack sizes are growing rapidly, according to Cisco[3], the peak DDoS attack size in the first half of 2018 was a dramatic 1.7 Tbps, a 179 percent increase from the first half of 2017 although there was a decrease in size in 2017 in comparison with 2016.
Types of DDoS Attack
Generally, DoS and DDoS attacks can be divided into three types:
-
Volumetric attack which is the most common type of DDoS attack and we have described it so far and includes UDP floods, ICMP floods, and other spoofed packet floods[4].
-
Application Layer attack which aims the topmost layer of the OSI network model which is the closest to the user’s interaction with the system. Attacks that make use of the application layer focus primarily on direct Web traffic. Potential avenues include HTTP, HTTPS, DNS, or SMTP[5]
-
Protocol attack which focuses on damaging connection tables in network areas that deal directly with verifying connections. By sending successively slow pings, deliberately malformed pings, and partial packets, the attacking computer can cause memory buffers in the target to overload and potentially crash the system. A protocol attack can also target firewalls. This is why a firewall alone will not stop denial of service attacks[5].
DDoS as a Service – DDoSaaS
In [6], researchers have reported 138% increase in DDoS attack with traffic more than 100 Gbps which involve IoT devices and easy availability of commercial DDoS service or DDoS as a Service for hire. For instance, it is possible to order a 5-6 Gbps DDoS attack lasting 10 minutes for 6$. DDoSaaS also know as booter or stresser can be used for knocking websites offline or perform stress tests on different network infrastructures, to give an illustration, Shenron Attack Tool which offers eight different packages which the cheapest one costs $19.99 and launch a 35 Gbps attack for 20 minutes with UDP and TCP traffic or vDOS Attack Tool which has thirteen different attack vectors available for DDoS Attack. The cheapest one costs $19.99 and gains access to 216 Gbps attack shared network.
Continue Reading – Part II: Distributed Danial of Service (DDoS) II
Last post: Security in IoT – Overview