Security in IoT – Distributed Danial of Service (DDoS) II
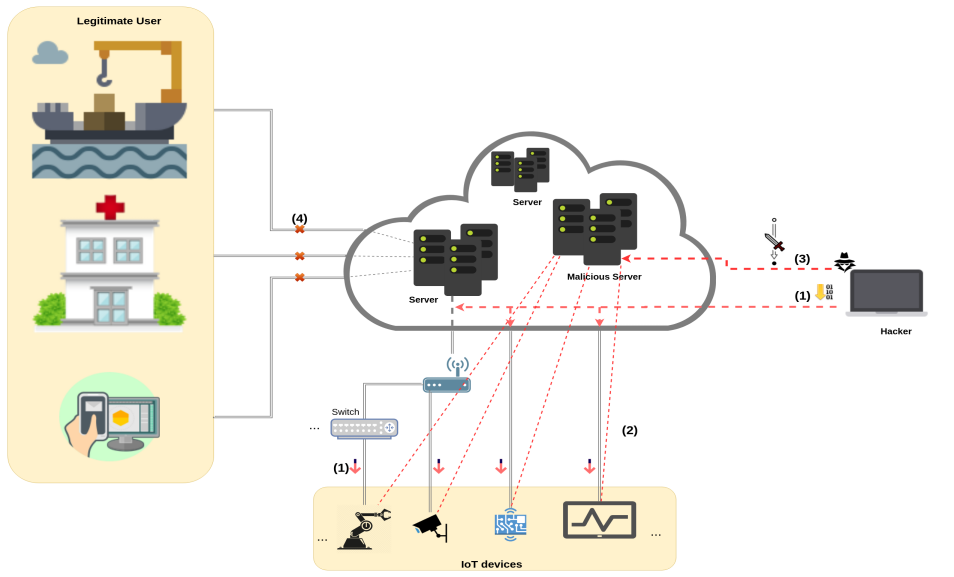
This post is the second part of the last post and will describe the architecture along with characteristics of Malware especially Mirai and Hajime. Characteristics of IoT malware As mentioned before, the IoT device should get the Malware in order to participate in DDoS attacks. Most of the malwares are Linux based and has limited
