Security in IoT – Overview
In this post series, I’m going to talk about security in IoT devices and I try to clarify the following aspects and questions about them:
- Security for IoT devices. Motivation and why people should care about the security of their IoT device or more general, for every device that can connect to the Internet?
- IoT system model and threads in this model
- Danial of Service attack (DoS and DDoS)
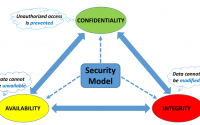
- CIA Security model/solution
- Most popular communication protocols for IoT devices and do they satisfy CIA model?
- Case study and tips about the security of Mongoose OS (Malicious code injection)
The goal in this post is to give you a general overview of security in IoT devices and why it is important to consider it whenever we buy, build or use devices that can send or receive data from the Internet. IoT devices in one hand intend to make our lives more convenient, but on the other hand, expose many security vulnerabilities and threads that cause cybercriminals and privacy leakage and it is important to protect them against different malicious attacks as well as personal data leakage.
What hackers want
A hacker can hack a system for different reasons, earlier it was for bragging rights, but nowadays, these attacks are carried out by organized criminals for financial gains or for revenge or extortion or activism[1]. Besides, IoT devices are collecting different information such as financial, health, etc. about users and organizations, therefore hacking these devices can also lead to privacy issues.
Why IoT Devices are suitable for attacking
IoT devices are particularly advantageous for creating botnets/malware and there are many points in support of this view, the most important one is that they are constantly connected to the internet whereas computers and smartphones may have somehow interval for connecting to the internet. Moreover, due to the rush to the IoT market, many device vendors neglect security in order to deliver convenient usage. Another key thing to remember is that IoT devices are powerful enough to produce DDoS attack traffic and as a result, they have been widely used in different attacks. Also, they usually contain critical data for communication to the server such as private/public key, endpoint, etc. which are interesting for hackers and they can use them to access the IoT server and try to disrupt services or steal user data.
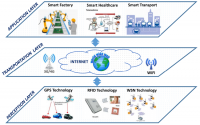
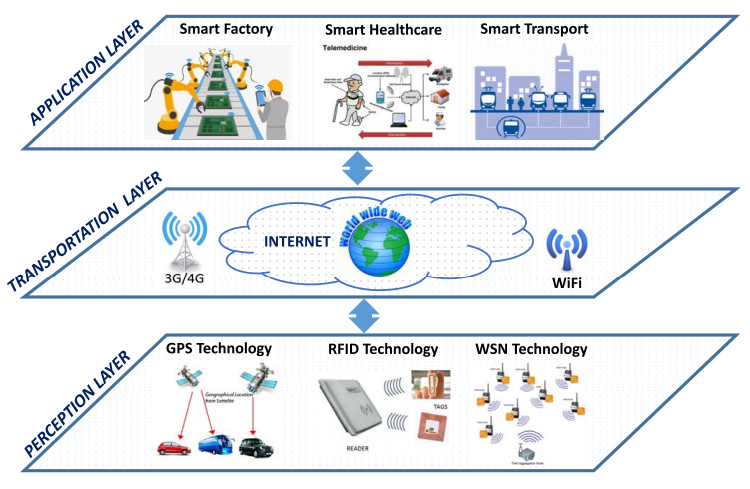
IoT System Model
A generic IoT system can be fully represented by using three main key layers and are represented in Fig. 1. The first layer, perception layer, is related to the physical IoT devices such as sensors, actuators which collect and process data using different technologies like WiFi, RFID, Serial, etc. The second one, the transportation layer, transmit the information which received from the perception layer to the cloud or any specific information processing system through existing communication networks[2]. And the last layer called application layer which provides services for the user/customer. In each of these layers, specific technologies have been used and bring some possible security issues which some of them will be mentioned in the next section.
Common attacks for IoT devices
There are some security threads which are common between layers like Malicious Code Injection and DoS attack which will be described next post. The primary purpose in this post series is security thread coming from the perception and application layer which can be in a form of hardware or software attacks. The main hardware thread for preception layer divided into categories: (a) Node Tampering such as semi-invasive attacks and fully-invasive attacks[3] in which the hardware will be damaged. Fig. 2 represents an example of the semi-/fully-invasive attack on Yamaha YMF262 audio IC. (b) Malicious Code Injection and non-invasive attacks in which the hardware will not damage and can be done through program/debug interfaces, power analysis, fault injection, etc[4].
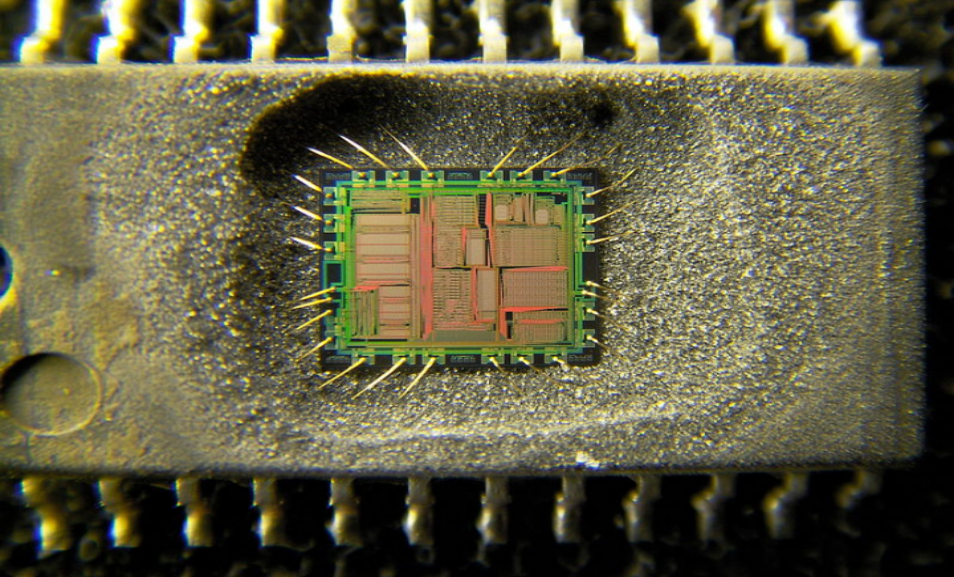
On the other hand, software attack contains a vast variety of attacks including DoS, routing attack, impersonation, data transit attacks which refers to attacks on the confidentiality and integrity during data transmission such as sniffing and Man-In-The-Middle(MITM). In MITM, attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other[5]. For instance hacking of a Jeep Cherokee[6] which connects to the internet through uconnect and its head unit expose a particular service and let’s do things like query information such as GPS location, etc. and also lets run commands for control the vehicle. Malicious Code Injection can also be done through Social Engineering attack which is based on human interaction and involves manipulating people to breaking normal security in order to access to network, systems, physical location or financial gain[8]. As an instance, injecting malicious code to the network can happen through opening a malicious Email(Phishing), Baiting, etc. It should be considered that intermediate malicious nodes might modify the right routing paths during the data collection and forwarding process[2] which causing data leakage or identity theft. In the next post, we will focus on DDoS attack and Botnets in application/perception and how Malware orchestrate a DDoS attack in IoT devices.
Continue Reading: Distributed Danial of Service (DDoS) I